ECE Assistant Professor and Yangbin Wang Rising Star Endowed Professor Farimah Farahmandi has received funding from the Office of Naval Research (ONR) in support of her 3-year project, “FAME: Fault-Injection Assessment and Mitigation of Microelectronics at Pre-silicon.” The $600k grant supports work which aims to counter hardware attacks on microelectronics by discovering the most vulnerable locations in a chip’s design in order to develop more efficient physical protection.

The Background
With the emergence of the Internet of Things (IoT) and edge computing that promises new and exciting applications from the military, naval, mobile, financial, transportation, and household sectors, security and privacy have emerged as major design challenges. The computing and sensing components in an IoT system, cryptographic hardware in embedded systems, reconfigurable field programmable gate arrays (FPGA) embedded systems, artificial intelligence (AI) accelerators, digital signal processors (DSPs), and microprocessors are all highly vulnerable to a myriad of physical and non-physical attacks. These attacks appear in different forms (e.g., information leakage, side-channel leakage, fault injection, physical attacks) and can effectively bypass the security mechanisms built into a chip’s design, thus putting systems at risk.
Fault-injection attacks in particular have become a major concern to the computer security community due to their powerful capability in tampering with critical features in a device and their ability to extract secrets, regardless of the mathematical strength and robustness of the security mechanisms. Through this type of attack…
“..typically requiring physical access, an attacker can momentarily tamper with a processor’s electrical inputs (e.g., voltage or clock). By violating the safe ranges of these operating parameters, a fault can occur within the processor, which can result in skipped instructions or corrupt memory transactions. If hardware or firmware is not intentionally designed to compensate for fault injection attacks, an attacker may be able to leverage a fault to undermine critical platform security functionality, such as secure boot.“ [ NCC Group ]
The Defense
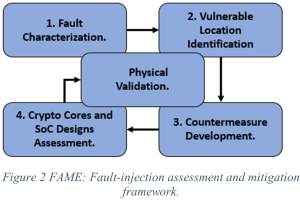
Dr. Farahmandi’s team defend against this kind of attack before the microelectronic devices are ever manufactured—as the title of the project suggests, “at pre-silicon”. Using both custom-developed simulation techniques and commercially available products, chip designs are probed and examined for vulnerabilities. The designs themselves can be put through the stresses experienced in a fault injection attack to simulate how they will react, thus enabling researchers to predict which elements in the chip designs are most likely to fail. Armed with this knowledge, Farahmandi’s group can develop countermeasures, safer designs, and then validate their augmented designs with actual fabricated chips.
The end goal of this project is to enable the production of hardware more resilient to various methods of fault-injection at a much more feasible cost.